
CYBER RESILIENCE
Nurture confidence in your security.


-
CYSIAM Pathway is an essential methodology for any organisation looking to improve its cyber resilience. Leveraging our bespoke platform, our consultants help organisations to strengthen their cybersecurity strategies with confidence and ease.
-
At CYSIAM, incident response readiness runs through the core of everything we do. No organisation is 100% secure, as evidenced by regular high profile breaches, and therefore we must consider that an attack is possible at any stage in its development.

We Use a Threat-led Approach
Any maturity / risk assessment that CYSIAM conducts begins with a threat assessment. Threat intelligence is key in understanding the context of the assessment we are undertaking, and prioritisation / criticality of the resultant planning. We don’t omit any assessment criteria in our reviews, we use threat intelligence to gain increased focus on certain areas in the same way that an attacker would.

Risk Assessment & Maturity Framework
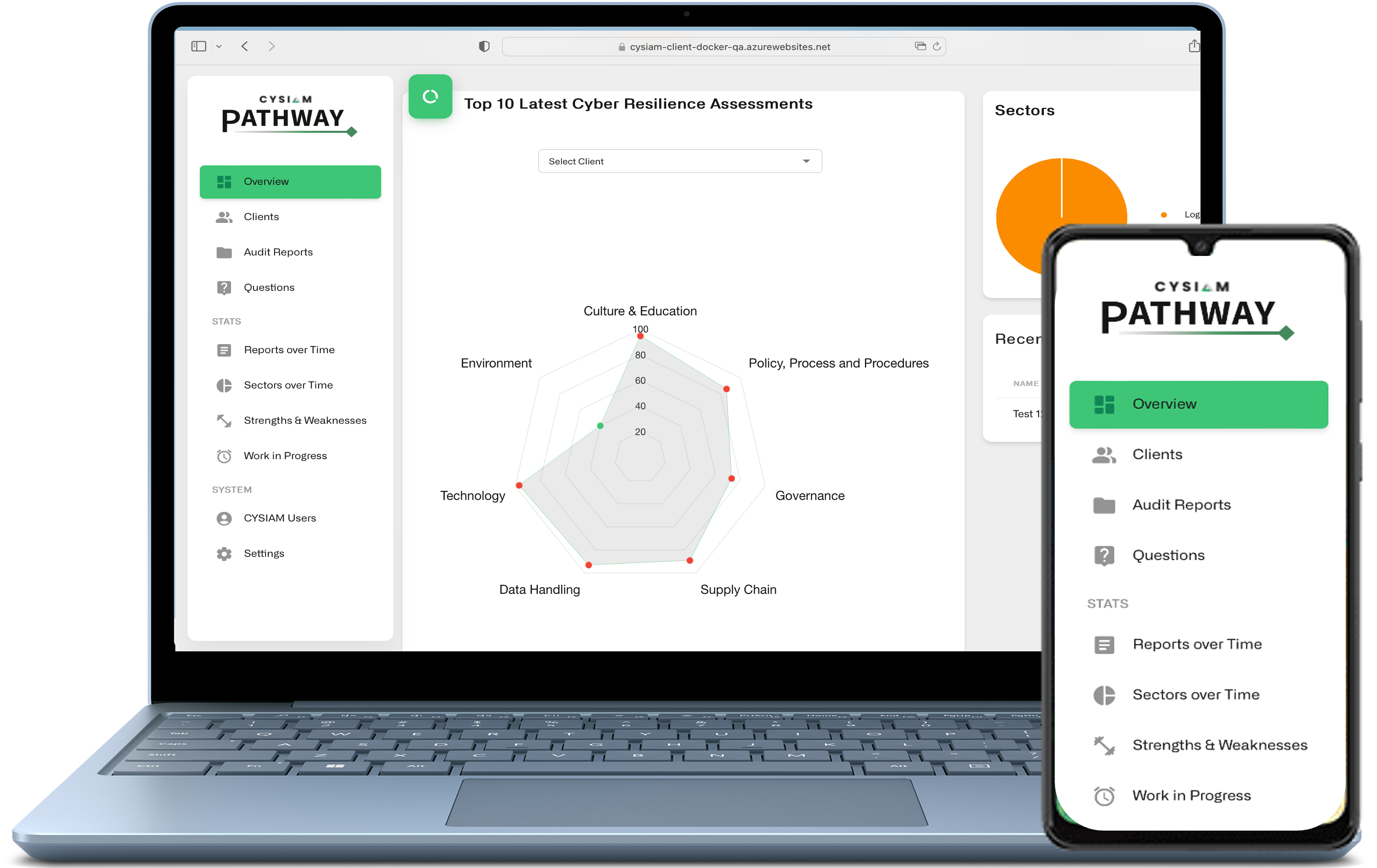
We assess your organisation against combined international standards, providing detailed metrics on your current risk profile and level of maturity. Our consultants help you to identify critical weaknesses that could be exploited by attackers, whilst our bespoke platform generates detailed reports with actionable recommendations.
-
Governance
Cyber-risk should be treated like any other business risk and should have board level ownership. This review will evaluate the approach to cyber-risk, how it defines roles and responsibilities, and if critical business dependencies have been identified along with the threats posed to them.
-
Policy, process & procedure
Appropriate documentation and working practices provide the necessary underlying foundation on which the correct business decisions can be made, whilst demonstrating compliance to relevant legislation and standards. Our review will evaluate existing policies and identify gaps in documentation and working practices that can be addressed to reduce cyber-risk.
-
Technology
Technology should comply with, and support, the security policies of an organisation. ICT teams (internal or outsourced) are usually focused on maintaining availability of the technology's functionality, and this can lead to mismanagement of technical security controls. We assess the 'real-life' approach against policies to identify any gaps (vulnerabilities). To this end, we can conduct vulnerability scans of the organisation's external and internal network and devices as part of a policy compliance assessment.
-
Data handling
Understanding the data that is processed is crucial not only for establishing and implementing the correct security controls, but also for legal compliance (GDPR). This review will confirm whether an organisation has identified the data it processes, transmits, and stores, and whether it has the necessary security in place to protect it.
-
Culture & education
People can be a critical weakness in cyber security but also a key aspect of defence. Understanding levels of awareness within an organisation and its workforce helps to identify areas of strengths and weakness and where to focus programmes of improvement. Culture plays an important role in the security of an organisation and our assessment will evaluate if cyber security awareness and understanding is embedded at all levels.
-
Physical environment
We look here at how physical access to an organisations ICT infrastructure is controlled, from server rooms to network access points to individual devices. Often the simplest method of attack is best and stealing or cloning an employee's door pass can gain vital access to sensitive areas of buildings. This is where digital and physical risks overlap, and we always advocate a holistic view of security.
-
Supply chain
Critical suppliers and third parties can introduce vulnerabilities to an organisation's business resilience and security. Due diligence should be carried out on critical suppliers and third parties to identify any risks associated with them or the services, products, or systems that they provide. The review will ascertain the level to which supplier risk is addressed within the organisation.



Whilst the CYSIAM Pathway framework is bespoke, it does cover the key aspects of several industry leading standards and regulations such as:
- NCSC Cyber Essentials & Cyber Essentials Plus
- ISO 27001
- NIST Cyber Security Framework (CSF)
- GDPR
- PCI DSS (only used if relevant to business)
