

Managing Supply Chain Cyber Risks
By James Kench – CYSIAM Chief Operating Officer
Employing good cyber practice, such as not using the same passwords on different applications and using multi-factor authentication (MFA) where possible is not just about protecting ourselves. In the same way as practicing good personal hygiene, such as washing hands helps others by reducing transmission of infectious diseases, good cyber practice helps reduce the risk that you will be used as a vector by a nefarious cyber actor (criminal, hacktivist etc) to obtain access into other peoples or companies’ networks.
Most reasonably sized organisations have recognised that they have quite a lot to lose if their data systems were exploited in some way. This could be a hospital with ICU machines connected to their network, a law firm with confidential customer data stored on servers, or an airline with an online booking system. Once this recognition has been established and the risk raised to a sufficient level, the organisation is likely to have put in place robust cyber defences such as firewalls, passwords, and MFA to protect its core functions. Attackers know this and rather waste time on a difficult target, they are increasingly focusing on supply chains as an easier alternative, a “soft underbelly” if you will.
Suppliers, such as outsourced software providers, website builders and IT managed service providers often have access to their customer’s critical data and systems making them a target. Cyber-attacks on these kinds of organisations are certainly on the rise. An August 2021 article in “Supply Management”, the magazine of the Chartered Institute of Purchasing and Supply, ran with the headline “Supply Chain Cyber Attacks to Quadruple”[i]. This is not a problem that is going to go away, and all organisations should recognise and manage this risk.
So, what should you do about supply chain vulnerabilities? Well, the first step is to recognise the risk and ensure that accountability for the risk is held at the highest level in the organisation possible, preferably the board. Don’t assume that this is simply an IT risk, it is a business risk and therefore requires a business solution.
Next, you should identify which of your suppliers are critical. You may not have the time, funds, or energy to treat your whole supply chain in the same way, furthermore, your actions need to be proportionate to the potential impact. Your critical suppliers will be unique to your organisation, but you could start by asking questions such as “do they hold or handle any critical data or other assets?”, “do they have priority to our internal systems?” and “if they failed could we still operate?”.
In parallel to identifying your critical suppliers you should be establishing a target cyber maturity position for these suppliers. We would use the CYSIAM 7 factor assessment to assist with this activity (Figure 1) but there are various models available. The ideal target cyber maturity position will be unique to the nature of your business and your appetitive for risk. For example, it may be that you care less about assessing your supplier’s physical environment because their remote working policy means a low level of maturity in this area is sufficient, or that because they only have 3 employees you care less about assessing their culture and education because it presents less of a risk to you.
Once you have established (a) your critical suppliers and (b) their target cyber maturity positions, these suppliers should be assessed to establish their current level of cyber defence capability. Then a joint action plan should be drawn up to deliver the necessary change between current and target maturity levels.
Delivering this change becomes your cyber maturity improvement programme. Again, we would use the CYSIAM 7 factor assessment at this stage as a measure of cyber defence maturity. The gap between current (dark green) and target maturity levels (light green) can be illustrated well using a radar or “spider web” diagram as shown below:
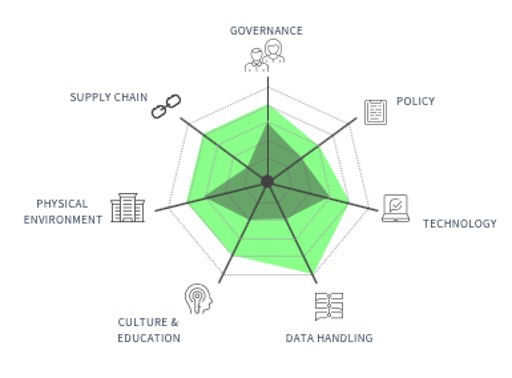
Figure 1 – CYSIAM 7 Factor Maturity Assessment for Suppliers
The important point is that this assessment should be used to agree joint actions and objectives with your critical suppliers, aimed at bringing the cyber defence capability up to the necessary level of maturity. The joint actions and objectives should then be systematically implemented and periodically reviewed by both parties to ensure continued and sustained change.
Non-critical suppliers should still be included in any cyber maturity improvement programme just in slightly less depth. Engagement with this category of supplier should be developed over time as part of a planned Supplier Relationship Management initiative. Initial steps could be to include mandatory compliance to recognised cyber standard(s) such as Cyber Essentials, as a contractual requirement, request evidence of regular internal audits on cyber procedures and practices and requiring the holding of appropriate cyber insurances.
In addition to the above, the NCSC’s 12 principles are a great guide and can be found here: https://www.ncsc.gov.uk/collection/supply-chain-security. As the page says, implementing the recommendations and principles will take time, but the investment will be worthwhile. Developing the cyber maturity of your supply chain will reduce the risk to your business, your supplier’s businesses and ensure that you are better placed to respond to this ubiquitous and long term threat.
[i] Juliette Rowsell, Supply Management, 3rdAugust 2021

DOWNLOAD THE PAPER
The Evolution of Ransomware
