
The Threat: BlackMatter
By Jack Lea – Senior Technical Consultant
In the aftermath of the ransomware attack on Colonial Pipeline in May 2021 that crippled the US transport and energy infrastructure, owners of Ransomware-as-a-Service (RaaS) groups ran for the hills. US and/or Russian law enforcement had taken swift action to dissuade and punish ransomware threat actors. Realising they had bitten off more than they could chew, DarkSide – the RaaS responsible for the pipeline attack – immediately ceased operations and freely offered decryption tools to their victims as their infrastructure was dismantled by an unconfirmed law enforcement agency[i]. Babuk, another RaaS, stepped away from the ransomware spotlight to concentrate on data-theft extortion instead, claiming to have handed over their source code to another team[ii]. Popular Russian-speaking cybercrime forums – XSS, Raid and Exploit – announced that they would no longer harbour discussion threads related to ransomware schemes and recruitment. And finally, after REvil had unleashed chaos by attacking Kaseya’s remote management software, they too went to ground – suspending their data leak blogsite and payment portal (albeit, temporarily).
But in this withdrawal, arose a new player – BlackMatter.
Wasting no time at all, BlackMatter (BM) boldly stated in their first post that they would be seeking targets with a revenue of at least $100M, in English speaking countries, with networks consisting of 500 – 15,000 hosts. Large companies with large amounts of cash at stake.
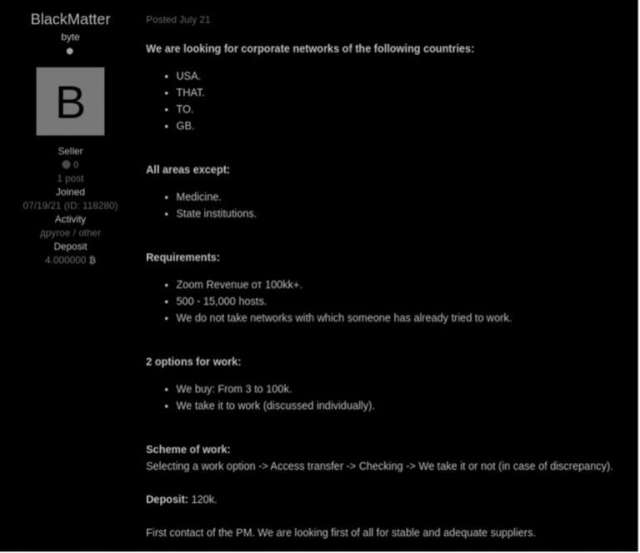
(Source: The Record) – BlackMatter’s account on Exploit Forum
According to the threat actor’s public blog, the ransomware group had built in “the best features of DarkSide, REvil and LockBit”. This was later expanded upon in an interview by Dmitry Smilyanets of Recorded Future and a spokesperson of BM[iii]. BM stated that they had improved upon REvil’s ‘SafeMode’, adding that it had been “weak and not well thought out”. They took parts from LockBit’s “implementation of the codebase” and “borrowed the structure of the admin panel” from DarkSide.
Though highly targeted ransomware attacks do occur, the main goal of most RaaS operators is profit. This means the initial stage of an attack will likely involve widespread scanning and exploitation of server-side vulnerabilities, watering hole attacks, exploit kits or even spam campaigns. The main objective of BM is to encrypt the victim’s data and hold it to ransom. According to CISA (Cybersecurity and Infrastructure Security Agency), once the BM ransomware reaches a target machine, it uses previously compromised embedded credentials to enumerate all running processes and services and then uses the LDAP and SMB protocols to access the Active Directory and discover all hosts on the network. BM then leverages the embedded credentials and SMB to remotely encrypt all hosts and shared drives as they are discovered.
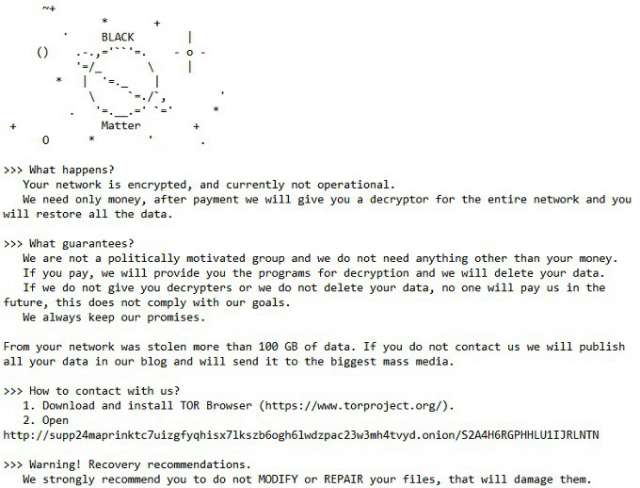
(Source: Twitter @rivitna2) – Screenshot of BlackMatter’s ransom note
The threat actor states in their website that they abide by a set of rules; not to attack hospitals, oil and gas, critical infrastructure, defence, NGO’s and governments. A measure to avoid the ever-increasing vigilance of law enforcement over critical infrastructure. These rules are likely to be in response to President Biden’s announcement in June where he spoke of 16 sectors that should be “off limits” to cyberattacks.
However, it appears these rules are being loosely followed – if at all – as a recent attack by BM has left an Iowa-based farming services provider incapacitated and ransomed for $5.9M. New Cooperative provides farming technology and software platforms to mainly grain farmers, a service that is considered critical to the US food supply chain. It could be argued that BM are technically following their own rules, as they have only identified power plants and water treatment facilities as critical infrastructure under their definition. Nonetheless, a definition highly criticised.
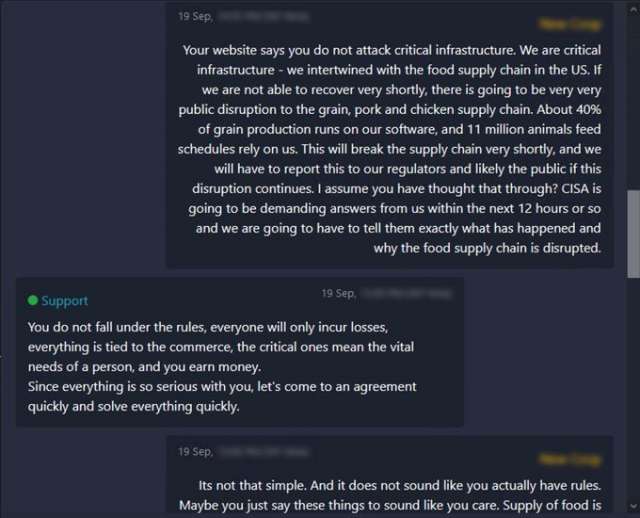
(Source: Twitter) – Screenshot of New Cooperative and BM’s conversation
For a ransomware group that is no more than 4 months old, they have been involved in several highly publicised cyberattacks. These are just the incidents that have managed to reach the headlines and appear on their own data-leak site. The number of attacks that are currently underway or have already been settled privately could be far higher. If the group truly is a descendant of DarkSide, it is reasonable to expect far more from them in the coming years.
All is not lost though, CYSIAM have put together a list of mitigations that businesses can implement to reduce the risk of ransomware attacks.
- Protect Important Folders with Controlled Folder Access[iv] – Controlled Folder Access protects data by checking access request of applications against a list of trusted and known apps.
- Strong Password Controls and Password Managers – Demand all accounts (e.g admin, service accounts etc) have strong and unique passwords. To ensure passwords are not reused across the enterprise, incorporate password managers to create and retain credentials.
- Enable MFA for all services where possible. Especially accounts with access to critical systems.
- Use an Endpoint Detection and Response (EDR) Solution – EDR detects malicious processes that have started to run on the endpoint and can automatically respond by blocking the process.
- Implement a robust and tested Backup and Disaster Recovery plan, including adopting the 3-2-1 Backup Strategy –
- 3 copies of the data exist (1 original, 2 are backups)
- 2 copies are kept on different media (cloud, NAS)
- 1 of the copies is kept offline and offsite
- Implement effective policies and procedures that incorporate playbooks which align with staff awareness training.

DOWNLOAD THE PAPER
The Evolution of Ransomware
